Remote access is hidden installation. RMS remote access
What is this product as a remote manipulator SYSTEM? This is a very interesting application that can interest many users. For example, those who want to make sure they make their comrades in their operating systems. So let's get acquainted with this application. Especially since it was produced by Russian developers.
Description
Remote Manipulator System - What is this program? Maybe she is not worth breaking her head over her? Often it is customary to think that this is true. But some users really find the program application.
Remote Manipulator System is a kind of application that allows you to use the remote control of the computer. Quite often, such a system is used in a variety of companies and firms. From the computer-server you will be able to monitor changes (and promote it) of all systems under the control of the application. For example, it is easy and easy to climb on someone else's computer, change the settings in it, remove / set some utilities, and with all this remain unnoticed. Many are interested in: Remote Manipulator System - What is it? Useful program or malicious? It all depends on the situation. In general, it was invented for a safe remote control, but some are capable of applying it not for the best purposes, but for hacking someone else's operating system. So it is necessary to use this program with caution.
Installation
We have already figured out what the Remote Manipulator System is. Now you need to understand how to install this application and make it work. The main problem is that this process consists of two parts. First stage - installation of the server (main computer), the second - client part.

Let's start with the fact that we will make your computer dominant. Only then you can think about questions: "Remote Manipulator System - How to use yourself? How to send her victim?" To begin with, you will have to find the utility setup file. Download it, only then proceed to action. It is worth noting immediately - there are several options for installing the client. The first is manual. It passes in the same way as the usual installation of the program on the computer. The second is remote. It is carried out from the administrator's computer, relevant for large firms. If you prefer to use Remote Manipulator System at home or in a small office. Preferably select the first method.
We install the server
On your computer, run part of the RMAN-Server. This is the server part of the installation. That is, we make the main computer from our operating system from which you can manage clients. The Remote Manipulator System is installed in exactly as well as the usual application.
The main process will be after initialization. Installing a server on a computer. In the application window that opens, go to the section "Connections" and select "New Connection" there. The first tab will have to specify the server name, as well as the IP address of your computer. You can only use one field - or name, or address. Preferred to fill all the "empty places". In principle, the problem is solved. It remains only to explore possible functions, and then learn them to use.

Client
Remote Manipulator System - How to send a sacrifice? And how can you do so that the application makes it? It is interested in users who are interested to cling in other people's computers. Unfortunately, if you can not independently configure and install the utility, then problems may arise. Well, if the victim has problems with a computer - you can offer him remote help with Remote Manipulator System. Just enough to give you access to operating system.
After convincing the victim in the installation, ask him to put the RMAN-Viewer file on your computer. And then make a small setting. Or rather, the search for your server. For this, as in the past case, you will have to click on "connections", and then select the "computer name" or its IP address. This step will allow you to detect the server. Ready? Remote Manipulator System program almost completes the initialization process. It remains to do a few simple steps.
Now in the list of connections in the Sacrifice application, your computer must select, and then select "Remote Setup" on the toolbar. Now the address of the location of the distribution (RMAN-Server) is specified, and then clicks on "Configure". In the window that appears, you can specify the access password. As practice shows, it is not necessary to do it. Let the victim retain the change - and everything is done. You can manage a stranger computer.

Functional
Well, the main task came to the end. Remote Manipulator System is worth the victim on the computer. And now you can manage it remotely. The main thing is that the application has been launched at that moment. As a rule, this happens just automatically. The program is prescribed in autorun when the computer is turned on. But what can this utility?
To begin with, this is a remote computer management. That is, with the mouse and keyboard cursor. Sometimes it is a very useful intake. In addition, you can simply watch what is happening in the operating system, enjoy special command line, Task Manager and Device, as well as control the power of the computer and the start of applications.
The main features of Remote Manipulator System is the ability to connect to a webcam or microphone (at the same time including), as well as the server according to the schedule. Text chat is also available. But such an opportunity is, perhaps, each application remotely manage computers.

All features are easy and simply implemented using the control panel in RMAN-Server. There is enough just to click on the desired buttons, configure the observation window, and then implement your ideas. True, you will need to have an Internet connection. In networks, it is preferable to select "Standard Mode". It is in additional settings. That's all, now you can remotely manage a stranger computer.
Removal
But if you do not need Remote Manipulator System, how to delete this application? This question often concerns only customer customers. From the server, the program is easily deleted and simply - with the initializer. But on client computers this process is with difficulty. Even if you, with the help of the usual way, delete the program, it will still work. After all, the client part of it is a kind of virus that is eliminated with great difficulty.

So, Remote Manipulator System will have to be deleted as a malicious object. To begin with, get rid of the client part it, which is set as the application of the same name. Removed? Now go to the "Task Manager", and then complete the processes "RFUSClient" and "Rutserv". Next - you have to clear the autoload and the system registry. This will help CCleaner. Run, mark all sections hard disk And other possible items, then click on "Analysis". A few seconds of expectation, and you can har down on "cleaning". That's all.
Antivirus or program for catching spies to try to delete it is not worth it. Remote Manipulator System is not marked as a malicious or dangerous object. So you should not spend time on scanning.
RESULTS
We learned that I represent Remote Manipulator System. This object, to be honest, can be useful, and dangerous. If you do not have any secret intentions about the client computer, it is better to use any less dangerous and "depart" application.

Here, to be honest, leaders TeamViewer. So think several times before installing the "remote manipulator". Sometimes it is very difficult to expel this application from the computer. If it fails to remove it from the autoload, you will have to use the system's rollback and its reinstallation.
September 13, 2013 Odnocrylov Vladimir 2
Today we test the decision to manage the remote desktop Remote Manipulator System 5.5. The kit consists of several utilities, including the "Client" and "host" modules. With their help, you can establish a connection with a remote computer and remotely control the operation of all its functions. In addition to this in RMS 5.5 there is a chat, video call, the ability to edit the registry and much more. Read the details in our review.
Video Review Remote Manipulator System 5.5
Composition of the Remote Manipulator System 5.5 software package
With the development of the Internet, local LAN and increasing the speed of the connections increasingly need to refer to remote computers - it doesn't matter whether you are a system administrator in a company with a large PC Park, or just want to help a friend living at the other end of the city. In any case, remote desktop management programs are not losing popularity, and their developers are all expanding functionality. And today we will look at one of these solutions - versions 5.5 At the time of testing.
 Image of the RMS 5.5 box
Image of the RMS 5.5 box
This software package includes the following modules:
- RMS Host - After installation on a remote host, it allows you to connect to it to control and configure. The server has no active windows other than the parameter menu.
 Setting RMS Host 5.5
Setting RMS Host 5.5
- RMS client - program for connecting to RMS Host.
- RMS Agent - RMS package that does not require installation and administrator rights to start. The program immediately connects to servers to generate ID and password, withdrawing the appropriate window, and the rest is not much different from the standard host.
- Mini Internet-ID server - A server that is placed locally and allows you to use the Internet-ID without accessing Tektonit servers.
 Information about RMS Mini Internet-ID 5.5
Information about RMS Mini Internet-ID 5.5
Additionally available in the client of the program so-called MSI configurator - This is a step-by-step master of the creation of three types of distributions (the usual MSI packet, a distribution kit of an automatic installation and RMS agent) From the package RMS Hostdownloaded from the official site.
Selecting a Distribution Type in MSI Configurator from RMS 5.5Choosing a package type, you can set additional options - it is even possible to send an email message to the ID of the installed client.
Distribution Settings in RMS 5.5If some of the required fields are not filled, the wizard will return you to the desired step, and after the package will be formed and you can choose the location of it.
Selecting the Save Modified Distribution RMS 5.5In general, it is convenient, especially if you need to work with multiple computers and not all of the user has full access rights. In addition RMS Agent You can with help MSI configurator Make a logo and name of your company.
Impressions from working with Remote Manipulator System 5.5
In fact, this software works on the "server-client" principle, as well as many other similar programs, and copes with it quite good. Allowed not only to connect and manage the computer / to monitor user actions, but also use a lot of useful tools:
- File transfer. This is achieved using a dual file manager window, in which you can copy the data on both the host and your computer.
- Power management. In essence, you get access to the possibilities of shutdown and restart PCs, including Wake On LAN functionality.
- Task Manager - Monitoring and management of processes on a real-time remote PC.
- Terminal - A simple terminal for the command line OS on the computer managed.
- Running programs Allows you to open executable files and documents on behalf of a specific account, including imperceptible to the user.
- Inventory - Access to system information.
- RDP. - Connecting to a remote PC using Microsoft RDP protocol.
- Chat - Minimalist text messenger to communicate with users of connected computers.
- Screen entry- Screen video clip log.
- Message. This option allows you to output a specified message on a remote PC in a separate window - for example, you can notify the user about the technical papers.
 Creating a message in RMS 5.5
Creating a message in RMS 5.5
- Remote camera Allows you to receive a video stream with a remote PC, and despite the specialization in the cameras, you can select any capture device available on the remote computer.
- Remote Registry. The registry editor of the remote PC is an extremely useful tool for the system administrator.
- Audio and video chat Allows, like "chat", communicate with the user of a remote PC, only this time using the microphone and / or webcam. True, other capture devices module also sees, so for normal operation it is always worth selecting webcam themselves in the settings.
As for the functionality, intended for control, it is expressed by a special panel at the top of the operating window, which is shown when the mouse cursor is shifted. Separately, it costs to mark the display of the screen and the ability to prohibit the input of the user deleted computer itself - it eliminates the technical support operator from the control of the mouse or simply from the curious eye if you need to configure the PC in the absence of a user. For a person "At that end of the wire", this is expressed in the fact that the screen is simply flooded with a solid white background, and the computer does not respond to keystrokes and the actions with the mouse.
PC Control Window in RMS 5.5 Remote Control Function Panel RMS 5.5The connection itself is not ignored - for each saved connection, you can set a plurality of parameters, including optimization for the speed of a network connection or, for example, color settings for a remote screen. There is also such an interesting feature as a connection through the host: you can specify the host to which you are connected as an intermediate node, and to access RMS hosts to it local network. This allows you to configure computers in networks with limited Internet access.
Connection Settings in RMS 5.5Even for Microsoft RDPs, separate settings are allocated - by the way, they correspond to the standard, so that compatibility issues RMS. With other Hosts, RDP will not be.
RDP Connection Settings in RMS 5.5There is such a useful opportunity as a remote setting. RMS Host. - You just choose this option, wait for about 5-10 seconds, and then you can freely change the module settings RMS Host On the connected PC.
Connection for Remote Host Settings RMS 5.5 Remote Host RMS 5.5 settings
Remote Host RMS 5.5 settings
Provided and license transmission mode - you can use the client to send a remote RMS Host A copy of your key, enter a new key or to withdraw an existing license.
Select the transmitted license in RMS 5.5General settings RMS client Radiats, but tanks - nine tabs are collected strictly structured options for the functioning of the client module.
Program Remote Manipulator System (RMS) allows " view the remote screen and control the keyboard and the mouse as if remote computer is directly in front of you" Thanks to it and programs with similar functionality, hackers quickly form botnets. In the hacker forums in the huge supply of suggestions for the sale of remote access to computers of victims at very affordable prices. As wrote on one popular resource " Such attacks are used not only for the extraction of the already familiar benefit (passwords, money), but also for the sale of people with an excess of some hormones - access to computers of girls who are often located in front of the computer».
In this article we will look at how to detect and remove Remote Manipulator SystemIf it was installed secretly from you.
In the main window of the Covert interface, in the upper right corner, there is a network monitor that provides a list of all active computers. If the process appeared on this list rutserv.exe.So you are monitored using the RMS program. If there is no this process in active connections with the network, then you should check the applications that wait for the timer connections or by the command. Quite often, remote access programs and spies are there. To see the waiting connections of the application, press the left mouse button on the "Appendix" column header or in the context menu, select "Connections", as shown in the screenshot below.

Function " System services"Let you see that remote access to your computer provides service RmanService..

In the list of system processes that gives a function " System processes", We find three processes RMS: ratserv.exe, rusclient.exe, rfusclient.

Secret observation of you is detected. How to delete RMS from a computer?
We found out that remote access provides the RmanService service installed in the OS. You need to remove it to make it impossible. In the system services monitor, call the context menu by right-click when you hover over the service name and select the "Delete" item, as shown in the screenshot.

There are situations where you need to leave a remote observation program on your computer, but you want your actions to remain invisible to RMS. In this case, add a file name to the "threat database" rutserv.exe.. When you start the Covert program, network connections are automatically analyzed and, if they are brought to the database of threats, they are blocked. The computer on which the RMS control module will stand is a client program, the assignment of which in connecting and monitoring your computer will receive a message about failure. It will not be able to set a reuse within your work inside the protected platform of the disguise.

All your actions will be hidden from remote viewing. Once you close the disguise program, RMS will restore remote access with your computer and will see on your computer everything you see.
Check if you are following you using RMS.
I recently had an intrusive idea to try to make my RMS assembly with a completely hidden installation and further hidden control.
In the internet, there are many controversial reviews about this - some write about meaningless due to the large variety of alternative methods (keylogs, stylists, etc.), others, on the contrary, represent this method, as a great variant of the hidden remote multifunctional control. Someone earns on this, selling the RMS assembly. There are even disassembly between competitors with subsequent deunionization. For example, offering its services LiteDem0 turned out to be: and VINJECT is the author of this topic:
Spoiler
Hidden RMS [Remote Administration]
Good day!
Today we will make a hidden assembly of Remote Manipulator System (Analog Radmin, TeamViewer)
Immediately I warn you that it is quite difficult to collect, especially beginners.
Video presentation how it works hidden RMS.:
View on YouTube.
I will try to explain everything step by step and available.
RMS (like Radmin, TeamViewer, etc.) performs the same feature - remote administration (i.e. control) computer
What can RMS know?
All its functions are listed here:
Management and observation
-File manager
-Text Chat
-Task Manager
-Connecting through Internet-ID! (just like TeamViewer)
-Device Manager
-Connecting to the command line
- screenshot on schedule
-Rodyted text message
- Support of several monitors
- Advanced installation
-Wake-on-Lan
-Tended registry.
-Function "Run"
- Connection to the Web-camera.
- Caverium
Integration with firewall
Let's start with the listing of what is the assembly:
1. Fully hidden installation (the screen does not blink unlike Radmina)
2. After starting the installer counts
3. All assembly files are hidden / systemic, the victim will be more difficult to notice something
4. An additional IP is sent to you, but it will not need it, most likely, since we will use the Internet ID
5. Weight will be ~ 2.8MB
6. This assembly is partially taken by antiviruses (how to make not falling - write to contacts)
So let's start collecting:
I. Setting up RMS server
First of all, download the archive
Attention! The archive is a password
Password for archive:
-
Open the R folder, run the Server.exe file, install. Upon completion of the installation, the program will start:
The security window appears in front of us:
Click Change / Set - Enter the password, let's say 12345678RMS
Go to the Authentication tab, should be tick - level 3
Next, click OK! All, the window disappears.
The next step for us will be the configuration of the server
In the lower right corner, click right-click on the blue icon
Configuring Internet Id Connection
Click to get a new ID, something similar is appearing:
The next step for us will be the second part of the server setting:
Open Start, Programs, Remote Manipulator System - Server, Settings for R-Server
There will be two steps, the first we have passed ("Safety").
2. Run mode - automatic
3. Settings, remove all ticks, only to "prohibit closing RMS", also in the Logging tab must be removed.
4. Licensed key - Enter this:
-
5. Close the settings
We open the directory where the server installed, and select the following files:
Copy, create a folder somewhere, insert everything there.
It is in this folder that we will have all the most interesting, then I will call this folder "New Folder"
We continue to work. Now we need to export our settings with passwords and all settings.
To do this, we need to do the following:
For xp, win + r: regedit
For 7, simply in the "Find Programs and Files" row, enter Regedit, and OK
Go here: HKEY_LOCAL_MACHINE / SYSTEM / Further export Remote Manipulator System
And specify the path of our created folder, (Specify the file name - sets) to which we copied our server files, that's what you should get:
By itself, the sets.reg file is the settings file, all your settings are stored there if you want to change something, you only need to replace this file by doing all previous steps.
II. Editing installer
Well, they switched to the main part.
We highlight install.bat, right-click - change
(The first half of the code is used to remove the previously installed Radmin, rem_cam on the sacrifice, and if it was previously RMS, we don't need someone, too, also had access to a computer other than us).
There are two simple steps:
1. Create mail on Yandex (!):
2. Please do not tupit here, so that there are no questions later!
Find it almost at the very end and edit it for themselves:
### Login ### is only login, without adding @ yandex.ru, ### password ### - 12345678, here you clearly-show your data from registration in Yandex.
Close, save.
Select the setup.exe file in the new folder, right-click the archive.
We allocate all that is in a new folder (except setup.exe, of course) and drag into the open window. Successfully added files to the archive.
As a result, you should get out this:
Copy somewhere our setup.exe file.
You can remove everything else from the folder.
III. Completion
So, we open the R folder, install the file viewer.exe, through it we will connect to the "victim" on the Internet-ID.
Important!
If you are going to throw your assembly to several "victims" and immediately, then the Internet IDs will have problems, as it is assigned to one build for one computer.
If you are going to distribute the hidden RMS massively, then in this case you need to connect to each "victim" by IP
As I personally advise you to use this assembly.
You throw her any one sacrifice, she sets it. Next, you can via the Internet-ID (which you copied above) connect. Did everything you need on the sacrifice on the computer and then delete the assembly from the computer's computer
For this you need:
Connect to the victim and choose the "Starting Program" connection - the sorridge - the victim go to the Windows \\ System32 directory there find the file de.exe, select. (Check the "Hidden Start" checkbox)
The file de .exe is included in the assembly. This is a county file that fully removes the hidden RMS assembly from the computer.
After starting this file, the victim is better to check whether the assembly retired (for this we are simply trying to connect again), if we cannot, it means the assembly was successfully retired and we can use our assembly on another victim just as on the first.
This is done in order not to conflict between two computers with one Internet-ID.
A large advantage of this assembly will be the fact that the connection will be 100%! Even if the victim has a dynamic IP (or for NAT "Ohm).
Also, this assembly is integrated with the firewall. In the settings, you can enable traffic savings, in this case everything will work will be launched and less traffic eats.
Not less than the presence of an embedded RMS servers scanner. If you suddenly lost your sacrifice with dynamic IP, you can easily find it by scanning the IP range in which it is (for example, 92.72.0.0-92.72.255.255)
In general - try, write reviews, throw thanks
Optionally, creating a downloider
What actually represents this downloider and what is it needed for?
This.exe file, which immediately after starting it, downloads the file and installs, after starting it counts, without leaving no trace
So, let's begin!
All you need is in the downloader folder
So, we need to register a server on Yandex.
You already have a mail on Yandex, where IP come. From this account, we register our server where we will pour our assembly.
For this:
1. Go to your account on Yandex
2. Switch by reference http: //narad.yandex.ru/
3. Click "Create a site" (We do not need a site, only file manager)
4. When our site is created going to the file manager, ****. Narod2.yandex.ru/FileManager/
5. Select "Download File", upload our RMS assembly
6. After the file is loaded, there must be such a gray link "Reference" button, press, copy.
Suppose we already have a server on Yandex, on which our file lies. Excellent, go on.
Next, unpack our downloaded archive, open the Link folder, the winupd.bat file is to change.
### Link ### - address to file
### downloaded "FileName ### - File Name
Batch File: open our batch file - winupd.bat
Save US: Leave as it is
The rest put as in the picture, it should work out like this:
Options tab:
In the Include tab, add a wget.exe file
INCLUDE Tab:
The next step for us will be the room Winupd.exe file in the shell, which will drop it and then count it.
File Load.exe, Open the archive, drag the winupd.exe file to the Load.exe file
Everything! Our downloider is ready!
For non-pass and convenience, you can make someone our file under the guise of a crack, patch, pictures, etc. (I immediately say, it is impossible to create an installer with an extension.jpg ,.mp3, except before it fights back in the victim's registry it is better to use s)
Changes in Express RMS:
Simplified setting (login and password enter in the textbook)
- After rebooting, re-send IP
- In the installer, only 6 files are now:
- Installation goes much faster
Please do not go into a personal with a request to give a key on which restrictions on all issues, as well as new assemblies, write to me for contacts (below)
Restressed archive
View on YouTube. new version of the assembly
For any questions / consultations / learning, contact:
Mail: [Email Protected]
Skype: vinject.
»We looked at a functional product to manage a computer via the Internet, in this article we will turn on how to connect to the remote computer.
So, we are faced with the task to help a friend in installing a program, each other city and is not very sacrificed in the computer, but it has the Internet.
Step 1 - Download and Run RMS Agent
- Dictation by letters or helmet by Samil, Skype to a friend direct download address - http://rmansys.ru/download/agent.exe;
- It launches the downloaded Agent.exe file (I note that the program does not require the administrator's rights and runs around the brandmaur). After a couple of seconds, your friend sees the program window on the screen:

And this is all, you don't need anything else to do anything, ID and password, he tells you! With the shudder I remember TeamViewer and with the need to press a dozen buttons and wait the seconds 40 before the unidentified program will start.
Step 2 - Download and Run RMS.Viewer5.5Ru.MSI
- You download customer management module - http://rmansys.ru/download (RMS Remote access - full version);
- From the downloaded archive, install - rms.viewer5.5ru.msi, the viewer label appears on the desktop (green monitor);
- Run the program:
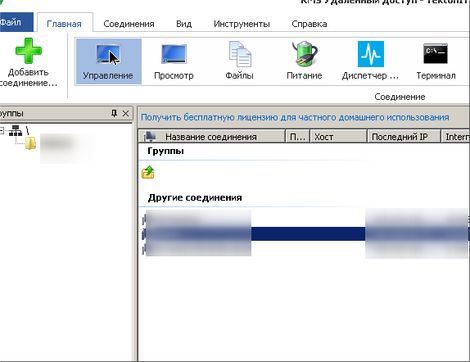
Right-click - Add a Compound, call an arbitrary connection name, enter the Internet ID dictated by another and click "OK". The program will make a connection, requests a password that we will tell us again and that's all, we have connected:

If you click a mouse to the top central part of the screen, then the control panel will be saved, you can run the file manager on it, turn off the keyboard to the client, so that you do not interfere, resize the screen size, etc.
Advanced work in RMS remote access
By right-clicking on the connection and selecting the Properties menu item, the connection property is displayed.

As you can see on the Advanced tab there are a number of very useful features, for example, you can disable the Aero interface during the conk, block the client and the client mouse, set up the color (downgrade for weak machines) and much more.
Also pay attention to the Safety tab. On the client side, in the agent you can rigidly set a permanent password, and in the client in this tab to register this password and thus have constantly access, which is very convenient.
Little comfortable cunning in working with RMS
The fact is that it is not necessary to set the client a host program, so that you can always go to it, you can copy the contents of the host folder and configure yourself the batch files / CMD files. The syntax of the command line is as follows:
rutserv.exe with the following keys:
- / SilentInstall - Install the host service
- / SilentUninstall - Uninstall Service Host
- / Firewall - integrate with system firewall Windows XP / VISTA / 7
- / start - run server
- / stop - stop server
- / Config - Open Settings Window
- / PrinterInstall - Install the RMS virtual printer.
- / PrinterunInstall - Uninstall Virtual RMS Printer.
Attention! Host commands are executed only on behalf of the administrator.